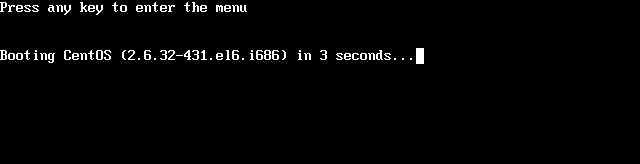Overview
It happens to the best of us. The root password for a particular server isn’t known, there are no other admin accounts available, and you need immediate access to the server. It may have been the result of a previous employee not documenting it or maybe it was lost. Either way, it needs to be reset.
Resetting the root password requires logging into single-user mode. To get into single-user mode we need to reboot the box. You’re obviously going to experience an outage, so be sure to inform your users.
The simplicity of resetting root’s password may alarm some of you. It’s important to remember that in order for you to do this, you need console access to the server. This is why your servers should be in protected area to begin with. No user should have physical access to your servers.
Resetting the Password
- Reboot the server.
- During the initial boot process, you will have three seconds to press a key to interrupt it. Do so to enter the Grub boot menu.
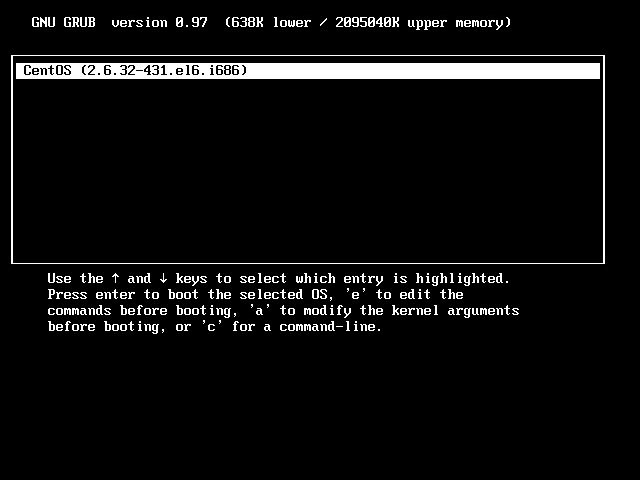
- Inside of the grub menu, ensure the appropriate boot kernel is selected, and then press ‘e’ to edit it.
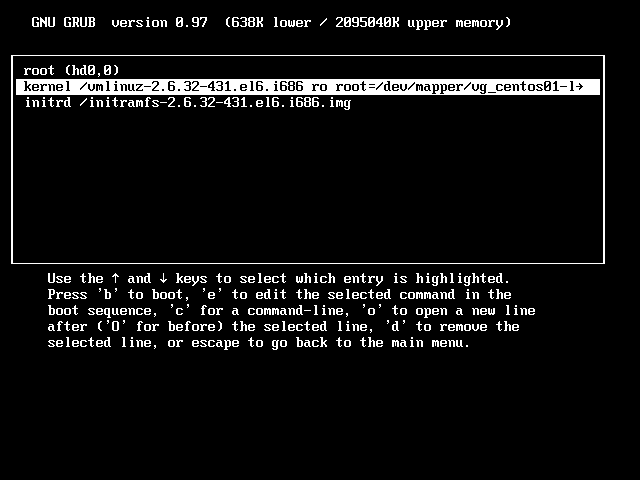
- Highlight the line that starts the systems kernel and then press ‘e’ to edit it.
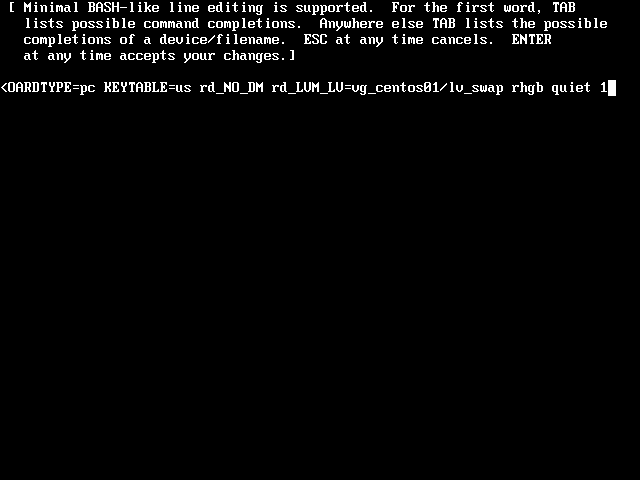
- Append the number 1 to the end of the line. This will force single-user mode when the system boots next. Modifying the kernel loader from within Grub is only a temporary change. The 1 will not be present the next time the system boots.
- Press the Esc key when done modifying the kernel line.
- Press ‘b’ to complete the boot process with the modified kernel settings.
- After the boot process completes, you will be logged in as root. To change the password, execute the passwd command.
passwd
- Do initialize multi-user mode, you can either reboot the server now or execute the init command with the appropriate run-level? Since this is a server without a desktop interface, I’ll change the run-level to 3.
init 3
Password Protect Single-User Mode
Seeing how easy can be to change root’s password may scare you, even with the server safely locked in your data center. Of course, not every office has data center. Sometimes servers are stored in storage closets that can be accessed by just about anyone.
We can force root’s password to be entered when booting into single-user mode. Although, this will definitely make it a lot harder to reset your password. I only recommend doing this when absolutely necessary.
If you do plan on password protecting single-user mode, make sure root’s password is documented and stored in a very secure location.
- Open the init configuration file into a text editor.
nano /etc/sysconfig/init
- Find the following line
SINGLE=/sbin/sushell
and make the following change
SINGLE=/sbin/sulogin
- Save your changes and exit the text editor.