Overview
Populating records in a hosts file is fine for very small environments, but as your environment grows beyond 10 computers, it starts to become a burden. How do you ensure that every client has the most up-to-date version of your hosts file? How do you know individuals haven’t modified them with your knowledge?
By deploying your own domain name server, you create a central database of IP address to host names. A single location for management of all your records. This is also creates a single point of failure, so I will also discuss creating a secondary server for redundancy.
This tutorial focuses on using the BIND DNS server for domain name services. BIND is arguably the defacto name server software for almost every DNS system in production. It’s used by many ISPs to respond to client queries from customers, it’s in many enterprise name server network appliances, and it serves as the building blocks to Microsoft’s Windows DNS.
Server Configuration
| Name | OS | IP Address | DNS Software | Role |
|---|---|---|---|---|
| NS1 | Ubuntu 13.10 | 172.30.0.60 | BIND 9.9 | Primary (Master) |
| NS2 | Ubuntu 13.10 | 172.30.0.61 | BIND 9.9 | Primary (Slave) |
Computer Environment
The environment being used in this tutorial consists of the following computers. These will need to be added to our first forward lookup domain.
| Name | Role | IP Address |
|---|---|---|
| Desktop01 | User Computer | 172.30.0.200 |
| Desktop02 | User Computer | 172.30.0.201 |
| Desktop03 | User Computer | 172.30.0.202 |
| Desktop04 | User Computer | 172.30.0.203 |
| FileServer01 | Network File Server | 172.30.0.100 |
| FileServer02 | Network File Server | 172.30.0.101 |
| MailSerer02 | E-mail Server | 172.30.0.102 |
Planning Your Domain Name
Before we can even start configuring our domain name server, we should have a good idea of how our domain will look. There are a few considerations that will impact the naming scheme you will use.
Forward Lookup Zones
These domain zones are used to convert names into IP addresses. You use one every time you access a website by it’s name. This is what we’ll be creating in this tutorial.
Reverse Lookup Zones
When you need to convert an IP address into a host name, you configure a reverse lookup zone. It’s used a lot for name verification when all you have is an IP address.
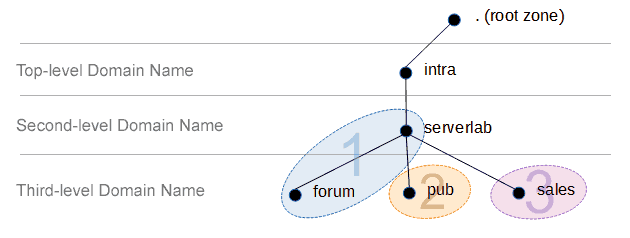
Naming Your Domain
There are a few rules you should follow when deciding on the name of your domain.
- A domain name must contain between 2 and 63 characters before the punctuation.
- A domain name can only contain the letters A-Z, the digits 0-9 and hyphen (-)
- If it’s for internal hosting only, it should not end in .com, .net, .ca, .org, or any other top level domain name (TLD). An example of an internal TLD is .intra.
- It should have a minimum of two domain levels – mydomainname.tld.
For this tutorial I will be using the domain name of serverlab.intra. It will be used for hosting internal records only.
Name Server Types
There are a few types of roles for a name server. In this tutorial we’re only going to focus on two – the master (primary) and a slave (secondary). The following list describes the most popular name server roles.
| Role | Description |
|---|---|
| Master | This server is where all adds and modifications are done. It is what is called an SOA (Start of Authority) server. No records are zones changes can be made without its knowledge. |
| Slave | This server is allowed to host a replica copy of a domain zone hosted by a master server. You should always have at least one slave for redundancy reasons. The server will act as an authority of a domain when the master is not available. It’s only limitation is that you cannot add records to or modify the domain on this server. It is read-only. |
| Caching | A caching server doesn’t actually host any domains. Instead, it caches every lookup done by a client after it resolves a name. It resolves domains by forwarding the requests to other DNS servers, like your ISP’s DNS servers. The benefit of having a caching server is name resolution performance can be greatly increased. |
DNS Record Types
There are a large number of DNS records types that can be employed in your domain, each with it’s own specific service, like e-mail, computer host names, name servers, and so on. Here is a brief list of record types that can be used.
| Type | Description |
|---|---|
| A | Address Record Used to assign a domain name to an IP address. |
| NS | Name Server Used to specify the domain name of name servers for a zone. |
| SOA | Start of Authority The absolutely authority domain name server of a domain or entire zone. This is typically a master server. |
| MX | Mail Exchange This record specifies which server or servers host the e-mail services for a domain. Without this record, clients and other mail servers would not be able to determine your mail servers. |
Install and Configure BIND
Follow these instructions on both servers, NS1 and NS2.
- Install the required packages for BIND.
sudo apt-get install bind9
- Start the BIND service to enable domain name lookups.
sudo service bind9 start
Create Your Domain
We’re going to create our first zone file for our desired domain. The zone file is what will contain our name records for our domain. It’s a simple database, if you will, of names to IP addresses than can easily be modified with any text editor.
To make things easy for us, we’re going to copy a template.
- Log onto the primary server, NS1.
- Create the new zone file by copying an existing template.
sudo cp /etc/bind/db.empty /etc/bind/db.serverlab.intra
- Open the new zone file into a text editor, like Nano.
sudo nano /etc/bind/db.serverlab.intra
Your zone file should look similar to the example below.
; BIND reverse data file for empty rfc1918 zone ; ; DO NOT EDIT THIS FILE - it is used for multiple zones. ; Instead, copy it, edit named.conf, and use that copy. ; $TTL 86400 @ IN SOA localhost. root.localhost. ( 1 ; Serial 604800 ; Refresh 86400 ; Retry 2419200 ; Expire 86400 ) ; Negative Cache TTL ; @ IN NS localhost. - Modify the file to match your environment’s configuration. We need to set the Start of Authority server (SOA) – the primary name server for our domain name, the e-mail address of the administrator, the Name Server record (NS) for our name server (ns1), and a Address record for the name server (ns1).
; BIND reverse data file for empty rfc1918 zone ; ; DO NOT EDIT THIS FILE - it is used for multiple zones. ; Instead, copy it, edit named.conf, and use that copy. ; $TTL 86400 @ IN SOA ns1.serverlab.intra. admin.serverlab.intra. ( 1 ; Serial 604800 ; Refresh 86400 ; Retry 2419200 ; Expire 86400 ) ; Negative Cache TTL ; @ IN NS ns1.serverlab.intra. @ IN NS ns2.serverlab.intra. ns1 IN A 172.30.0.60 ns2 IN A 172.30.0.61 - Now we add the address records (A) for the computers in our environment.
; BIND reverse data file for empty rfc1918 zone ; ; DO NOT EDIT THIS FILE - it is used for multiple zones. ; Instead, copy it, edit named.conf, and use that copy. ; $TTL 86400 @ IN SOA ns1.serverlab.intra. admin.serverlab.intra. ( 1 ; Serial 604800 ; Refresh 86400 ; Retry 2419200 ; Expire 86400 ) ; Negative Cache TTL ; @ IN NS ns1.serverlab.intra. @ IN NS ns2.serverlab.intra. ns1 IN A 172.30.0.60 ns2 IN A 172.30.0.61 desktop01 IN A 172.30.0.200 desktop02 IN A 172.30.0.201 desktop03 IN A 172.30.0.202 desktop04 IN A 172.30.0.203 fileserver01 IN A 172.30.0.100 fileserver02 IN A 172.30.0.101 mailserver01 IN A 172.30.0.102 - Save changes to the file and exit the text editor.
Add Your Domain to BIND
- Open the BIND configuration file into a text editor, like Nano.
sudo nano /etc/bind/named.conf
- Add the following lines to the end of the file.
zone "serverlab.intra" { type master; file "/etc/bind/db.serverlab.intra"; allow-transfer { 172.30.0.61; }; };Type Specifies the name server type – Master or Slave. File The location of the zone’s database file. Allow-Transfer Specify which servers, by IP address, are allowed to download the zone file. - Save your changes and exit the text editor.
- Instruct BIND to load our new domain.
sudo service bind9 reload
Configure the DNS Server to Query Itself
In order for your domain name server to return lookups, it needs to be able to query itself. To do this we’re going to modify its client DNS settings.
- Open the resolv.conf file into a text editor.
sudo nano /etc/resolv.conf
- Modify it so that it contains the following lines.
nameserver 172.30.0.60 search serverlab.intra
nameserver Sets the IP address of the DNS server to be queried. You can add as many nameserver entries as you have DNS servers for your domain. search The search option is used to append the defined domain name to all of your single-label lookups – any lookup that contains a computer name without a domain name appended. For example, desktop01. This way you don’t have to type the entire fully qualified domain name, desktop01.serverlab.intra. - Save your changes and exit the text editor.
- Test your name resolution by ping a computer registered in your domain using its fully qualified domain name.
ping desktop01.serverlab.intra
- Another method of testing name resolution is to use the Dig tool. It returns more detailed results about your lookup.
dig desktop01.serverlab.intra
- The Dig command will return the following results, which shows the question, the return answer, and which DNS server gave the response.
; <<>> DiG 9.9.3-rpz2+rl.13214.22-P2-Ubuntu-1:9.9.3.dfsg.P2-4ubuntu1.1 <<>> desktop01.serverlab.intra ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 688 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;desktop01.serverlab.intra. IN A ;; ANSWER SECTION: desktop01.serverlab.intra. 86400 IN A 172.30.0.200 ;; AUTHORITY SECTION: serverlab.intra. 86400 IN NS ns1.serverlab.intra. ;; ADDITIONAL SECTION: ns1.serverlab.intra. 86400 IN A 172.30.0.60 ;; Query time: 1 msec ;; SERVER: 172.30.0.60#53(172.30.0.60) ;; WHEN: Fri Jan 17 23:28:17 CST 2014 ;; MSG SIZE rcvd: 104
Configure the Secondary DNS Server
- Log onto the secondary (slave) DNS server, NS2.
- Open the Bind configuration file into a text editor.
sudo nano /etc/bind/named.conf
- Add a zone entry for our domain zone using the following configuration.
zone "serverlab.intra" { type slave; master { 172.30.0.60; }; file "/etc/bind/db.serverlab.intra"; };Type Specifies the name server type – Master or Slave. Master Specifies the IP address of the master server. File Specifices the location of the replica zone database file. - Save your changes and exit the text editor.
- Instruct Bind to reload it’s configuration file.
sudo service bind9 reload
- Our domain should not be downloading to our secondary server. Check that it exits by navigating to the location specified in Bind’s configuration file.